Google users can now download their entire Web search history to a desktop, according to instructions posted on the company’s support site.”This gives you access to your data when and where you want,” Google wrote about the service.Google search history has been available to users for a long time, but the ability for individuals to download all of the data at once was released in January, according to Google spokesman Jason Freidenfelds.The service was first reported by an unofficial, third party blog called “Google Operating System” on April 18 and picked up traction online, according to reports.
Author Archives: securitips
How attackers exploit end-users’ psychology
At RSA Conference 2015, Proofpoint released the results of its annual study that details the ways attackers exploit end-users’ psychology to circumvent IT security.
“The Human Factor research validates the critical value of threat information—and provides insight into how, when and where attacks are taking place,” said Kevin Epstein, Proofpoint’s vice president of Advanced Security & Governance. “The only effective defense is a layered defense, a defense that acknowledges and plans for the fact that some threats will penetrate the perimeter. Someone always clicks, which means that threats will reach users. Proofpoint’s approach is effective because our systems can determine who those users are, where they are, and what’s happening in real time—and actively protect organizations with real-time automated threat response.”
Your Password is Too Damn Short

Unless your password is at least 12 characters, you are vulnerable.
That should be the minimum password size you use on any service. Generate your password with some kind of offline generator, with diceware, or a passphrase approach – whatever it takes, but make sure your passwords are all at least 12 characters.
Source: Your Password is Too Damn Short
Consumers think passwords are of no value to criminals
21 percent of respondents to a Kaspersky survey assume their passwords are of no value to criminals. Many often take the easy way out when creating and storing passwords. For example, only 26 percent of those surveyed create a separate password for each account and just 6 percent use password storage software.
However, passwords are the keys to an online account holders’ personal data, private life and even their money, which is very valuable to a criminal.
Despite the fact that passwords provide access to valuable information, the survey shows that respondents are not always careful. Specifically, 18 percent of those surveyed write down their passwords in a notebook and 17 percent freely share their personal account passwords with family members and friends.
“Even if you are not a celebrity or a billionaire, cybercriminals can profit from your credentials,” says Elena Kharchenko, head of consumer product management, Kaspersky Lab. “A password is like a key to your home; you wouldn’t leave your door unlocked, or put your keys where anyone could find them, just because you don’t think you have anything of great value. Complex passwords unique to each account, carefully stored in a safe place, will save you a lot of trouble.”
To protect accounts against unauthorized entry, Kaspersky Lab recommends the following:
- Create a unique password for each account: if one password is stolen, the rest will remain safe.
- Create a complex password that won’t be easy to crack even if cybercriminals are using special programs. That means using at least 8 symbols including upper and lower-case letters, numbers, punctuation marks and no pet names or dates of birth.
- Do not give your password to anyone, not even your friends. If cybercriminals can’t steal it from your device, they might be able do it from someone else’s.
- Store your password in a safe place. Don’t write it down on paper; either remember it or use a special program for storing passwords from a reliable vendor.
Source: Consumers think passwords are of no value to criminals
Russian government giving cybercriminals advanced malware software
The Russian government is reportedly providing advanced malware software to cybercriminals and organized crime groups.
“Russian nationalism and organized crime are being assisted by Russian state security,” said Ray Boisvert, former assistant director and the head of intelligence for the Canadian Security Intelligence Service (CSIS), in a statement to The Register. “The red lines have gone because of Ukraine. Organized crime is being told they can disrupt Western interests.”
Russia has been accused on multiple occasions of providing support to organized crime and hacker groups, willing to conduct cyberattacks against foreign targets. However, trying to catch perpetrators and hold them responsible for data breaches, cyberespionage, and other similar crimes is extremely difficult for US authorities.
The United States has been criticized for focusing on spy tools used by the NSA and FBI, instead of spending more time on cybersecurity – and it appears to finally have caught up to the government, with department agencies, financial institutions, retailers, and other lucrative targets suffering breaches.
Source: Russian government giving cybercriminals advanced malware software
How to choose a strong encryption password
When it comes to security, it’s only as strong as its weakest link. File security is no exception. You may choose the largest encryption key and the strongest encryption algorithm known to the mankind, yet if your password is weak, your files may become easily accessible.
Selecting a good encryption password is not easy. On the one hand, it should be non-and complex obvious enough to be hard to guess for others. At the same time, it should be sufficiently simple to remember (rather than write it down) for you.
What complicates the matter is that there are quite a few misconceptions around that make choosing a good password rather confusing.
For instance, whenever you are prompted to create a password, the system usually informs you about the minimum length of the password that it requires. It may create the impression that the longer the password, the more secure it is. This is not always true! It would be true if you were choosing a random combination of characters for the password, such as “lalskdue”, or “sdlifwelfkel”, or whatever other combination you might produce by typing arbitrary keys. The problem is, however, that more likely than not, you are selecting an existing word (a.k.a, a dictionary word), like “apple” or “orange” for the password. In such a case, if someone would try the dictionary attack on your encrypted data, it would make virtually no difference whether the word is short or long. It takes the same amount of time (give or take a few nanoseconds) for the computer to try “abc” or “antidisestablishmentarianism” as the password.
That’s why most systems insist that your password should contain a combination of the uppercase and lowercase letters, numbers, and special characters: such additions make the dictionary attacks much harder. However, they make remembering the passwords harder, too. What should you do?
There are several methods available for creating strong passwords that are easier to remember. One of them is the “first letters of a phrase” technique. Think of a phrase that contains several words, that you could remember. For example, it could be a line from your favorite Eagles song, like “Welcome to the Hotel California, Such a lovely place, Such a lovely face.” Take the first letter of each word, and combine them together: WttHC,Salp,Salf. Note that we’ve preserved the capitalization of the letters, and also kept the commas in the middle. The resultant password is almost as strong as a random combination of 16 characters, yet you should be able to remember it easily, as long as you remember the original phrase.
Another method is by creating artificial passphrases (rather than passwords), by combining random words from a dictionary. Take a dictionary book, open it on a random page, and write down a random word you like on that page. Open the dictionary on another page, write down another word. Repeat several times, then move the words around to create a phrase. (The phrase does not have to make sense!). For example, I just tried it and came up with: “Antisocial Pomegranate holds back Blue Herring” (Sounds fun, doesn’t it?) If you can remember such a phrase (including the capitalization of the words), you’ve got yourself a rather strong passphrase.
Yet another approach is to create complex and long passwords for each situation, and use some password management software to keep track of them, such as KeePass. When using a software password manager, you only have to remember the master password. Of course, the inconvenience of this method is that you always have to use the password manager to recall the passwords for you, but if you need to have many strong passwords, that’s a small price to pay for the security. And, of course, don’t forget to backup your password database, because if you lose it, you lose them all!
How not to destroy evidence
“In a bold and bizarre attempt to destroy evidence seized during a federal raid, a New York City man grabbed a flash drive and swallowed the data storage device while in the custody of Secret Service agents… [the suspect] was charged with obstruction of justice…”
Source: The Smoking Gun
USB Combination Lock – a security joke?
One large nation-wide retailer is selling the following item on its web site:
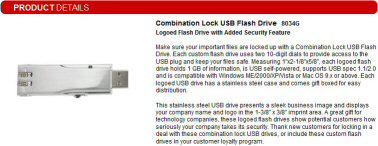
(click on the image to enlarge)
The web site urges you to get the device to “… keep your files safe”. Yet the combination lock contains only 2 digits (or just 100 possible combinations, from 00 to 99). How long would it take for someone to discover the combination, two minutes or maybe three???
For real security, consider a software encryption solution such as our USBCrypt. It lets you encrypt any USB drive (even those without any combination locks!) with strong AES encryption and thus make sure that no one would be able to get to your important files without the correct password.
