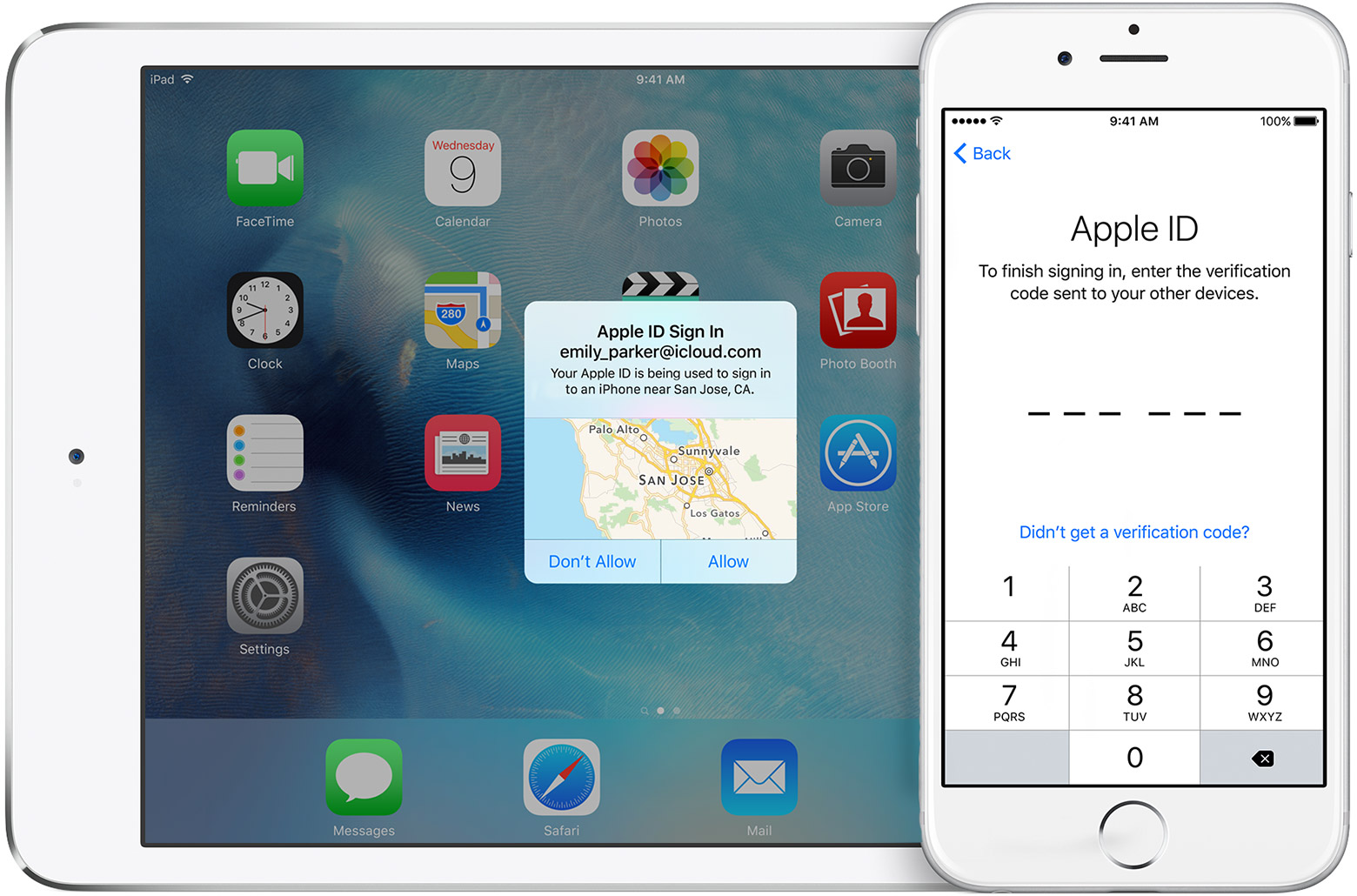
If you think that you are safe from fraud if you have enabled the 2-factor verification for a credit card, be aware that it can be bypassed if the thief steals not only the card but also your phone:
Phones, of course, can be made inaccessible with the use of passwords and face or fingerprint unlocking. And bank cards can be stopped.
But the thief has a method which circumnavigates those basic safety protocols.
Once they have the phone and the card, they register the card on the relevant bank’s app on their own phone or computer. Since it is the first time that card will have been used on the new device, a one-off security passcode is demanded.
That verification passcode is sent by the bank to the stolen phone. The code flashes up on the locked screen of the stolen phone, leaving the thief to tap it into their own device. Once accepted, they have control of the bank account. They can transfer money or buy goods, or change access to the account.
The solution? Change the notification setting of your messenger app not to display the SMS on the lock screen. Or better yet, if your bank supports it, instead of SMS, switch to using an authorization app.